Complete Guide On Data Encryption

Read this article to get complete knowledge about data encryption. Here we will show you how it works, its types and common methods to encrypt your data.
Encryption is the process of changing data from a format that converts a file from readable to encoded format. You can only read or access an encrypted file when it’s been unencrypted.
To keep your data safe, you should always keep your data encrypted. It is the easiest and most significant way to make sure that your computer’s information can’t be stolen or read by a third party.
Individual users and big businesses both use information security encryption to keep user information safe when it is sent between a server and a browser. These types of information could be anything from personal information to financial data.
So, in this article, we are going to explain the process behind it and the different types of it. Additionally, we will also explain how you can encrypt your data while surfing the internet or putting your credentials using symmetric and asymmetric techniques and with Virtual Private Networks for Windows.
How Does Encryption Work, What Are Its Types, And Common Methods To Encrypt Data?
Information nowadays is more desirable and accessible to hackers than ever before. This is why it is so important to protect it. Many businesses also have to meet data protection regulations, and others recommend you to use them. Encryption also helps in improving data security, protects your privacy, and stops people from getting their hands on it. And here we are going to show its mechanism, its types, and different methods.
How Does It Work?
When data or information is shared on the internet, it goes through several network devices all over the world. These network devices make up the public internet. As data moves through the public internet, there is a chance that hackers could get their hands on it and steal it. You can install special hardware or software to make sure that your data is safe when it is transferred.
Encryption is the process of changing human-readable text into an encoded text that can’t be read, which is called ciphertext. Encryption is done with the help of a cryptographic key. The cryptographic key is a set of mathematical values that both the sender and receiver agree on.
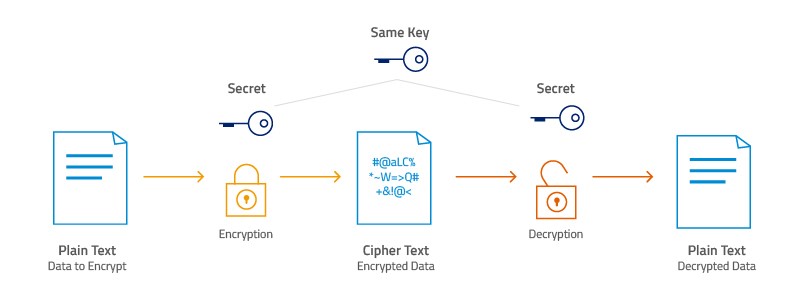
The recipient uses the key to decrypt the data, turning it back into plain text that can be read. Cryptographic keys that are more complicated are more secure because third parties are less likely to try to break them by brute force.
Types Of Encryption
Various types of encryption algorithms will encrypt your data according to the situation. When the old encryption algorithm gets insecure they make new ones to make the privacy stronger. Here are some of the best encryption algorithms that are most commonly used:
RC4 Encryption
It is used in WPA and WEP, which are two types of encryption protocols that are used in wireless routers.
Twofish Encryption
Twofish is one of the fastest of its kind. It can be used both in software and hardware.
RSA Encryption
In the beginning, RSA was considered the first asymmetric encryption method that was open to the public.
AES encryption
The full form of AES is Advanced Encryption Standard, and it was made to replace the original DES encryption method.
3DES encryption
3DES means Triple Encryption Standard. During the encryption process, the data is passed through the original DES algorithm three times. The word “triple” is used because this is a symmetric key algorithm.
DES encryption
People use the Data Encryption Standard (DES) to protect their data. This encryption algorithm is considered outdated, which isn’t good for today’s needs.
Different Techniques For Encryption
Symmetric and Asymmetric are the two most common techniques for data encryption. Their names show whether or not they use the same key for data encryption or data decryption.
Symmetric encryption keys
You can use this technique if you want to protect your keys, this is also known as “private key encryption.” In this method, the key used to encode is the same one used to decode, making it best for people and systems that are only used by them. Or else, the key will be sent to the person who wants it.
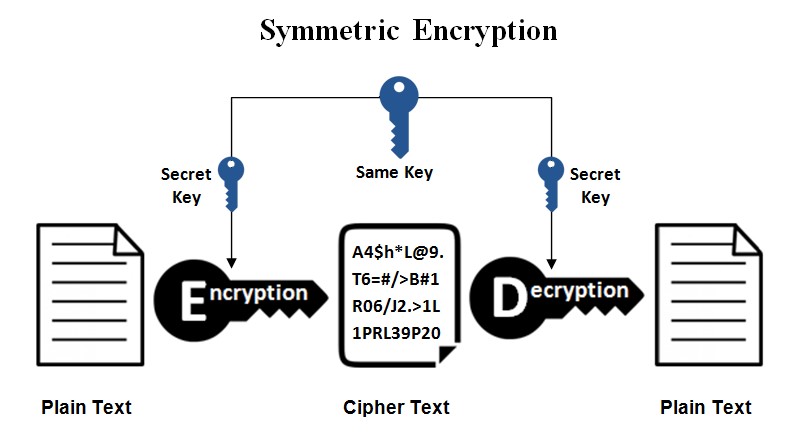
This makes it more likely that someone else will get their hands on it, like a hacker. This approach is more efficient than the asymmetric method, which takes more time than this method does.
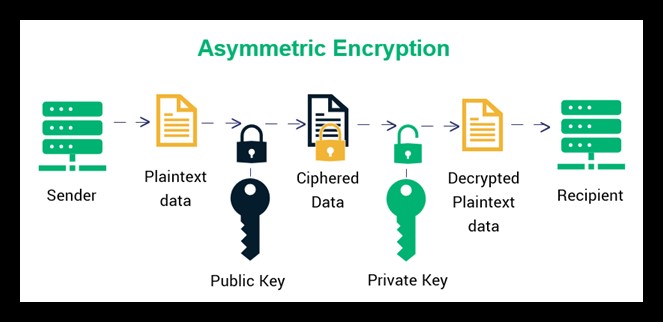
Asymmetric encryption keys
These keys are linked together by math. There are two public keys and one private key for this type. Each key is a large number that has been paired with another number of the same size, which makes it asymmetric. The private key stays with the owner. On the other hand, the public key can either be shared with people who are supposed to get it.
Summing Up
In cyber security, encryption is a way to keep private information safe from being stolen or hacked. Another important part of online safety is to use a good antivirus program. Spy apps, ransomware, malware, viruses, and the most up-to-date hacker tricks are all blocked by them. We hope this guide has helped you understand all about data encryption. If you have any queries regarding the same, mention them in the comments




